Multi-Factor Authentication - Required vs. Recommended?
By Josh Goodman
The required use of multi-factor authentication (“MFA”) for businesses to qualify for or maintain cyber insurance is a common topic these days. While MFA is always recommended, depending on how system access is setup will in most cases dictate if it is required. The following will provide some brief information that should provide clarity around when cyber insurance carriers require MFA to access company systems versus just recommending MFA.
What is multi-factor authentication?
For those unfamiliar with multi-factor authentication, it adds a layer of security that allows companies to protect against compromised access credentials. Through this method users must confirm their identity by providing extra information (unique security code) when attempting to access corporate applications, networks, and servers.
Remote Desktop vs. Cloud Computing
There are two primary methods for businesses to operate in a hybrid work environment to access their information and systems remotely. Remote Desktop access was the only solution for many years, but the developments in cloud computing have changed how everyone manages access. Both have vulnerabilities that businesses need to be aware of and insurance professionals should be discussing potential cyber risks with their customers.
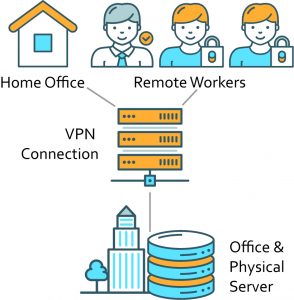
Remote Desktop
Remote desktop essentially means that any employee or independent contractor given access credentials will be able to utilize a Virtual Private Network (“VPN”) to access an organization’s server that stores all their files. In this instance MFA is required by almost all cyber insurance carriers and recommended by cyber security experts when logging into the organization’s network. If any individual’s remote login credentials were to become compromised, so too would all the information stored on that network. Also, a business’s IT team should layer additional security as cyber insurance underwriters will scan public networks for open ports for remote desktops. Remote Desktop ports must be closed and not available on public networks for 60 days or more to be eligible for most cyber insurance policies.
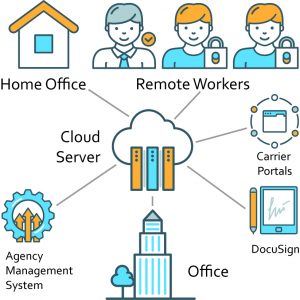
Cloud Computing
Cloud computing provides employees access to specific software programs or specific files rather to the entire network. Information is securely stored via a 3rd party offsite server that manages security and sets access permissions to the information. In the event of a cyber incident or compromised login it may be easier to contain the breach, as the bad actor may only have access to a certain data set and not the entire network. In this instance MFA is not required but it is still recommended by cyber insurance providers and cyber security professionals. We hope this provides greater understanding of when MFA is required versus simply recommended when discussing cyber exposures and coverage with your customers.